Twitter’s abuzz with the story of an ivy league economics prof being delayed on an airplane, because a fellow passenger spied him writing some partial differential equations. Not knowing what he was writing, she feared he might be a terrorist, and alerted the authorities. The authorities interviewed the guy, found him not guilty, and sent the plane on its way after over two hours of delay.
The press reaction is rightly outraged at the degree of stupidity and ignorance at display here — both on the side of the accuser, and on the side of the flight crew and authorities.
But amazingly, little bits of bias seem to be sneaking into otherwise well-meaning reporting.
Case in point, USA Today: Professor’s airplane math leads to flight delay, says the headline. No, no, no. It’s not the professor’s math that leads to the delay, but a bigot’s stupidity and fear of the unknown, combined with authorities who, out of an abundance of caution, deem the “foreign” guilty until proven innocent. Instead, the headline blames the professor and his equations. Yes, that headline might have been meant to be ironic — but it’s just too close for comfort.
The Washington Post certainly has the better headline writer: Ivy League economist ethnically profiled, interrogated for doing math on American Airlines flight. But then, deep in the (overall well-written) article, this gem:
That Something she’d seen had been her seatmate’s cryptic notes, scrawled in a script she didn’t recognize. Maybe it was code, or some foreign lettering, possibly the details of a plot to destroy the dozens of innocent lives aboard American Airlines Flight 3950. She may have felt it her duty to alert the authorities just to be safe. The curly-haired man was, the agent informed him politely, suspected of terrorism.
The curly-haired man laughed.
He laughed because those scribbles weren’t Arabic, or another foreign language, or even some special secret terrorist code. They were math.
Yes, math. A differential equation, to be exact.
[…]
His nosy neighbor had spied him trying to work out some properties of the model of price-setting he was about to present. Perhaps she couldn’t differentiate between differential equations and Arabic.
The author is obviously as aghast as anybody at the stupidity of what was going on; she goes on to paint the patent absurdity of the situation by finding various ways to quickly exonerate the professor in question — maybe Google him and find out who he is, how he won a price, how he is beyond reproach. But notice how, little by litte, that other concept sneaks in here? How writing maths (which really, any educated American ought to be able to recognize and accept) is somehow just a little bit different than writing Arabic? How, just maybe, the suspicion of terrorism is maybe deemed a tiny bit more justified if it were “Arabic, or another foreign language”? How, based on having written something, he’s now in need of being exonerated? How, maybe, somebody accused of doing maths on the plane without a public profile and without tenure track might take longer to be exonerated? How the story about “the paranoids are taking over, it was mathematics, not Arabic, for god’s sake” leaves that other sour taste behind?
Let’s talk about what really happened here. Somebody sat on a plane. He wrote, by all accounts quietly and peacefully. The person next to him was illiterate — or at least illiterate in the script or language he wrote. That was enough for the authorities to hold up the plane for over two hours. By itself, and whether he wrote in Russian, Greek, Arabic, Chinese, Korean, Japanese, Partial Differential Equations, abstract algebra, abstract nonsense, or even Perl or legalese, that’s an unequivocally absurd story of paranoia and bigotry. It shouldn’t matter which of those foreign or otherwise incomprehensible languages we’re discussing. The illiterate’s accusation that he was writing incomprehensibly, and therefore a terrorist, shouldn’t have passed the laughing test in the first place. The professor should never have even needed to explain or exonerate himself in the face of some authority.
To bring it to the point: The scandal here isn’t about mathematics. The scandal is that it took two hours to exonerate somebody from a suspicion of terrorism, a suspicion that was not just groundless, but based solely on the fact that they were literate, and their accuser was not.
Witch trials, anyone?
 The drama started with a 30min delay “due to catering”: Half of the carts for Economy class had gone missing, and even United wouldn’t launch on a 10h flight without food for the poor folks traveling in steerage. The half hour turned into two; the food was finally delivered. Pushback!
The drama started with a 30min delay “due to catering”: Half of the carts for Economy class had gone missing, and even United wouldn’t launch on a 10h flight without food for the poor folks traveling in steerage. The half hour turned into two; the food was finally delivered. Pushback!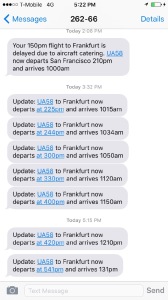
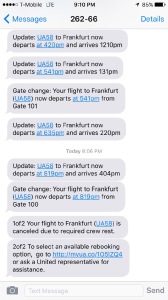 Cheers and applause. The plane taxis, we think we’re off — alas, the flight deck crew times out, on the runway. Off to park in some corner of the taxiway. An hour later, we’re back at the gate. “They explicitly don’t know whether they’ll re-crew the plane, or whether they’re cancelling”, I text. Doors aren’t opening yet, passengers pile up in the aisle, they just want to get off the damn plane. “They’re trying to make a decision in Chicago, it’ll be 10-15min”, the pilot announces. The United app notifies me that we’ll depart at 8:19pm, or some such — then, minutes later, the flight is cancelled “due to crew rest.” Brief confusion, people deplane, queue up in the departure hall. I learn I’m going to be rebooked (along with luggage, fingers crossed) if I just go home, so that’s what I do, to an unexpected night’s sleep in my own bed. People who need accommodation are less lucky —
Cheers and applause. The plane taxis, we think we’re off — alas, the flight deck crew times out, on the runway. Off to park in some corner of the taxiway. An hour later, we’re back at the gate. “They explicitly don’t know whether they’ll re-crew the plane, or whether they’re cancelling”, I text. Doors aren’t opening yet, passengers pile up in the aisle, they just want to get off the damn plane. “They’re trying to make a decision in Chicago, it’ll be 10-15min”, the pilot announces. The United app notifies me that we’ll depart at 8:19pm, or some such — then, minutes later, the flight is cancelled “due to crew rest.” Brief confusion, people deplane, queue up in the departure hall. I learn I’m going to be rebooked (along with luggage, fingers crossed) if I just go home, so that’s what I do, to an unexpected night’s sleep in my own bed. People who need accommodation are less lucky —  Same passengers, same plane, same crew, different flight number. There’s camaraderie: How are you doing, where did they put you up, what hotels were the parties in; the Hyatt turned off the water at 10pm; people in the lounge are boozing a little more than usual. On board, it’s “hello again” to the cabin staff — we’re all relieved that it’s finally a go. Double helpings of pre-departure champagne in business class, it’s party time and group photos on the upper deck. “We are cleared for departure.” The pilot jokes around, loud cheers. Push—
Same passengers, same plane, same crew, different flight number. There’s camaraderie: How are you doing, where did they put you up, what hotels were the parties in; the Hyatt turned off the water at 10pm; people in the lounge are boozing a little more than usual. On board, it’s “hello again” to the cabin staff — we’re all relieved that it’s finally a go. Double helpings of pre-departure champagne in business class, it’s party time and group photos on the upper deck. “We are cleared for departure.” The pilot jokes around, loud cheers. Push—